What is Phishing?
 It is a form of on-line identity theft. It can consist of any kind of fraud, which may result in the loss of personal data (e.g. credit card numbers, bank account data, authentication and passwords, etc.), almost always with a view to obtain economic gains and benefits.
It is a form of on-line identity theft. It can consist of any kind of fraud, which may result in the loss of personal data (e.g. credit card numbers, bank account data, authentication and passwords, etc.), almost always with a view to obtain economic gains and benefits.
How can it be Achieved?
The obtaining of personal data can be achieved in different ways, namely through:
- Fraudulent Copies of Original Sites
Copies of sites of bodies of a public-private nature (companies, financial institutions, banks, government entities, etc.) can be used by replicating their graphic aspect and functionalities (e.g. logos, banners, images, forms, etc.);
- Scam E-mails
Sometimes scam e-mails, apparently from known public-private bodies (e.g. banks, insurance companies, tax offices, on-line payment services, or even simply fromother persons, etc.) are sent to the user.Personal data is requested covertly in these e-mails. In these cases, it was seen that in the data collection process such e-mails may have malicious files or links attached which refer to forms for information collection.
Gaining and exploiting the victims’ trust in an attempt to obtain their personal data or another kind of sensitive information is a common feature in this type of fraud.
Other Features
- The contents of a phishing e-mail usually aim to trigger a quick reaction from its recipients. To achieve such, the criminal agent can use false pretences or the so-called “cover stories”, which can be, for example, an urgent request for some administrative document, etc;
- Through phishing messages, it is common for one to be asked to “update”, “validate” or “confirm” one’s personal data, on the pretext of avoiding some kind of security breach.
Examples of Messages:
This type of fraud has a wide spectrum of coverage. For example, in the banking sector, e-mails that may contain fraudulent scam messages are commonly used by criminal agents. The following are some examples of phrases:
- Please check the following payment information (…);
- Mr. (Name), for security reasons, your Home Banking access credentials need to be updated (…);
- Mr. (Name), “on-line account holder”, access to your account is currently unavailable (…);
- We regret to inform you but, for security reasons, proceeded to block access to your bank account. Call (telephone) to restore your access (…).
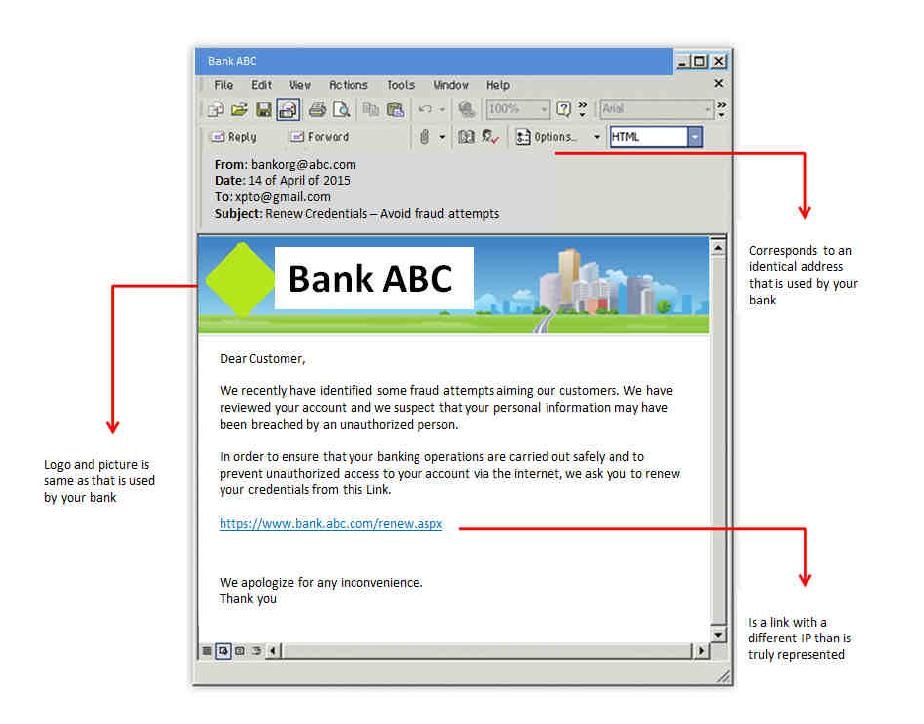
Example of a phishing e-mail:
As can be seen, besides containing a misleading story this e-mail also refers to the link (https://www.banco.abc.pt). This is a fraudulent link, which apparently has a secure “https://”. This can however be a replica of an original site.
Different types of information may be requested through this link:
- Information requested: full name /date of birth / full address / social security number / user name and password for on-line services / driver’s licence number / personal identification numbers (PIN) / credit card information (numbers, expiry dates and the last three digits printed on the signature panel) or bank account numbers.
- This information can be used to enable them tohave access to your financial accounts / open new bank accounts / transfer bank balances / request loans / use credit cards / and other services and products / shopping / access your personal e-mail account / receive tax benefits / obtain a passport / or hide criminal activities.
How to React?
If you receive a suspicious e-mail:
- If the scam story is linked or makes reference to known institutions or bodies, communicate the facts to them within the shortest possibletime;
If you receive a suspicious e-mail and unwittingly provided personal or financial information, follow these steps:
- Contact your bank and report what happened;
- Report the facts to the Security Forces or to the Public Prosecutor’s Office.
How to Prevent?
- Be suspicious of any e-mail or text message containing urgent requests for personal or financial information (financial institutions and credit card companies normally will not use e-mails to confirm a client’s information);
- Should you be wary of the true origin of the entity that sent you a suspicious e-mail, contact the “real” one through their official contacts, whereby using a telephone directory for such;
- Never e-mail personal or financial information;
- Avoid embedded links in a suspicious e-mail;
- Get in the habit of confirming the address of the official sites with those that are referenced in the e-mail from non-credible sources;
- Regularly update your computer protection with anti-virus software, anti-spyware, and firewall programs;
- A number of companies and institutions (e.g. banks, insurance companies, etc.) provide advice to their clients on how they may protect themselves from phishing;
- Regularly check your bank, credit and debit statements to ensure that all transactions are in conformity.
References:
- Law on Data Protection
Authors:
 Lieutenant-Colonel Paulo Jorge Soares dos Santos
Lieutenant-Colonel Paulo Jorge Soares dos Santos
 First Sergent Lino Pedro Morais Roque
First Sergent Lino Pedro Morais Roque